#6 Active Directory
By Christopher Melendez
Compare Active Directory to Azure Active Directory
We touched on Azure AD earlier while discussing RBAC, Custom Domains, and extending Active Directory identities into the Cloud. Now we must take a deeper look at the different types of Active Directory to understand what they offer. Active Directory is a huge topic to tackle and identity is now at the forefront of almost all security conversations, so I’m just going to touch on some of the most important concepts.
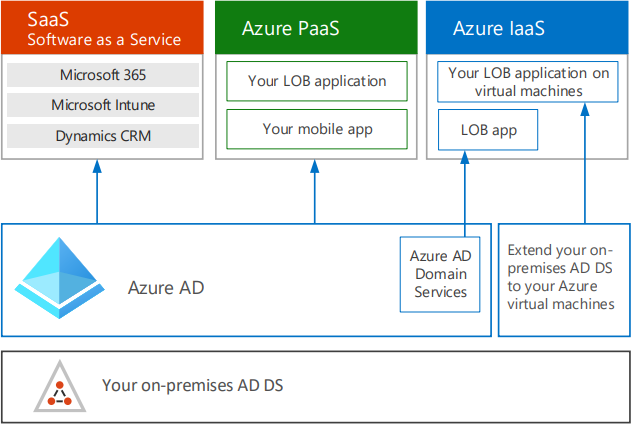
The 3 “flavors” of Active Directory are self-managed Active Directory Domain Services (AD DS), Azure Active Directory (Azure AD), and Azure Active Directory Domain Services (Azure AD DS). Even though the names are very similar, they are designed with different organizational needs in mind.
Active Directory Domain Services
Active Directory Domain Services Overview
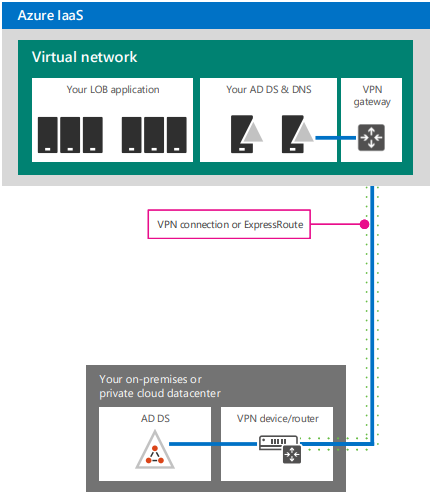
Deploy and manage Azure IaaS Active Directory domain controllers in Azure
Self-managed Active Directory Domain Services is your traditional Windows Server that you’ve had laying around your server closet for years. It provides services including domain join, group policy, LDAP, NTLM / Kerberos authentication, and trusts. Active Directory stores information about user accounts, computer accounts, passwords, and even email details. The directory, also referred to as a data store, contains information about all the objects that exist in the schema. Some of the objects include resources on file servers, printers, and line of business applications.
Azure Active Directory
What is Azure Active Directory?
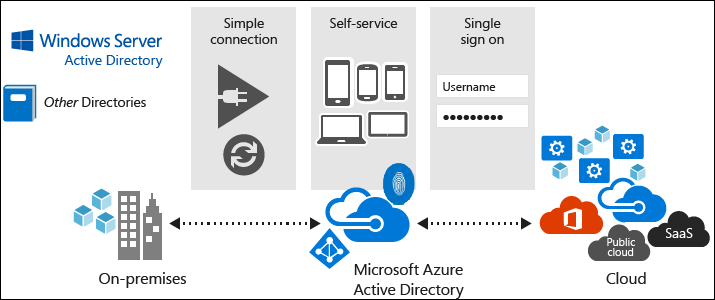
Manage identity and access in Azure Active Directory
Azure Active Directory (Azure AD) is the Cloud-based identity platform that provides the authentication services for the Microsoft SaaS suite including Office 365 and the Azure portal. The platform also provides mobile device management and resource management leveraging features like Conditional Access and Azure AD device join. Azure Active Directory does not provide the traditional services of LDAP, NTLM / Kerberos, group policy, Sites and Services, etc. Although it provides device identity with Azure AD Device Join, Azure Active Directory does not include server domain join capabilities.
Azure Active Directory Domain Services
What is Azure Active Directory Domain Services?
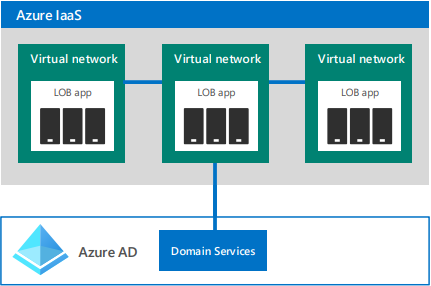
Tutorial: Create and configure an Azure Active Directory Domain Services managed domain
Azure Active Directory Domain Service (Azure AD DS) is a PaaS version of the original AD DS. It provides a managed domain services offering, with a subset of the traditional AD DS features. Like the original self-managed Active Directory Domain Services, Azure AD DS includes features like domain join, group policy, LDAP, and Kerberos / NTLM authentication, but it does not provide a full domain forest hierarchy. Azure AD Domain Services is not an extension of your existing on-premises domain/forest infrastructure. It provides synchronization of on-premises infrastructure leveraging a one-way outbound forest trust model. When Azure AD DS is deployed, Microsoft creates 2 virtual machines in replica set for resiliency. The two virtual machines are managed by Microsoft so there is no need to worry about patching and monitoring of the infrastructure and OS.
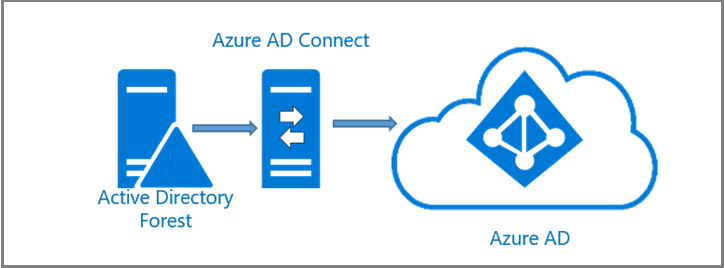
Azure AD Connect
Define a hybrid identity adoption strategy
Both Azure Active Directory Domain Services (Azure AD DS) and traditional Active Directory Domain Services (AD DS) can integrate with Azure AD using Azure AD Connect. Azure AD Connect is a tool that can be installed on a virtual machine that handles all the operations related to synchronization of identity data between your existing on-premises domain controller environment and Azure AD. This type of deployment is referred to as hybrid identity. Hybrid IT is a mixture of on-premises and cloud workloads. Traditionally, users would only access workloads on-premises, but things have change and users access applications in on and off premises now. Managing users in these scenes provides challenges, so Microsoft’s solution was to create a common user identity for authentication and authorization for all resources, regardless of location. This type of technology is known as single sign-on or SSO for short.
Comparison
I would have to say the biggest takeaways are: If your customer is going to be born in the cloud or is looking for 100% Microsoft cloud adoption and minimal IaaS, Azure AD with Azure AD DS for virtual machine and mobile device join is probably the best solution for you. If you’re working with a customer that has an existing on-premises or datacenter environment and probably won’t ever fully deprecate it, extending Active Directory with traditional self-managed Virtual Machine promoted to a Domain Controller could be your best option. I try to keep in mind growth, it would add additional complexity if your customer had to go through a large M&A and were limited to one-way outbound forest trusts. This is something that might be easier to overcome if it’s a small Azure footprint.
One thought on “10 Steps to get started with Azure for partners. #6”
I loved your blog article. Thanks Again. Want more. Jewell Tuley
Comments are closed.