#7 Networking in Azure
By Christopher Melendez
Configure and manage virtual networks for Azure administrators
You can imagine how big a topic networking in Azure is. Microsoft does us a favor by breaking Azure networking services into 4 “buckets,” the first being connectivity services. Connectivity services is what I would consider the backbone of networking fundamentals, providing the functionality to connect Azure resources and on-premises resources together. At the heart of it all is Azure Virtual Networks or VNets.
What is Azure Virtual Network?
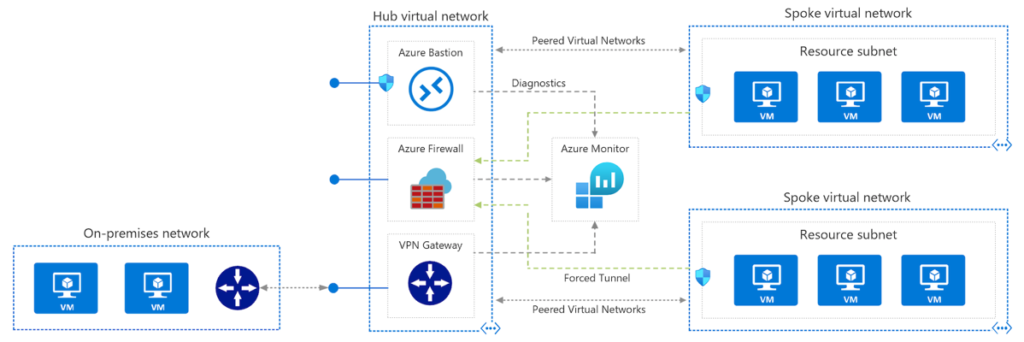
Azure Virtual Network (VNet) enables many Azure resources, such as Virtual Machines, to securely communicate with each other. It also provides connectivity to the internet, as well as on-premises networks. VNets provide a similar set of services like traditional networks with a network/subnet configuration, but they allow you to scale, and provide additional availability and isolation compared to traditional Datacenter networking. All outbound traffic is allowed by default in Azure VNets. You can assign a public IP address or a public Load Balancer and implement Network Security Groups or leverage Azure Firewall to create rules allowing inbound traffic to a resource.
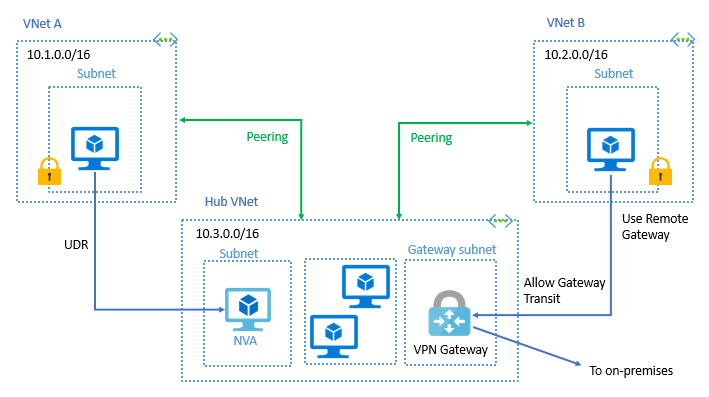
There are other services, some of them we’ve already covered in our 10 steps, like Azure Virtual WAN, ExpressRoute, VPN Gateway, but there’s also VNet Peering service. By default, VNet to VNet traffic is blocked, but subnets under the same VNet can communicate freely. VNet Peering provides the ability to connect virtual networks together, enabling Azure resources in either VNet to communicate with each other. This provides the ability to transfer data between VNets across Azure subscriptions, Azure Active Directory tenants, deployment models, and Azure regions.
Architect network infrastructure in Azure
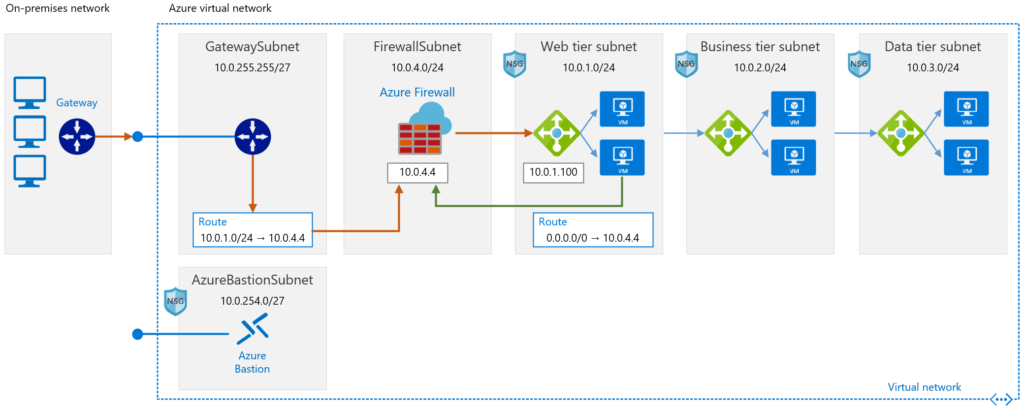
Application protection services is the second “bucket” Microsoft provides. It includes services like DDoS protection, Azure Firewall, Network Security Groups, and Web Application Firewall, to name a few. These services allow you to protect your applications and workloads utilizing a combination of services. Network Security Groups (NSGs) are like access control lists (ACLs), they can contain multiple inbound and outbound security rules that filter traffic to and from resources by source and destination IP address, port, and protocol. They can be applied to subnets and virtual network interface cards. Azure Firewall is a network security service that provides a single location for you to manage and apply all your NSGs.
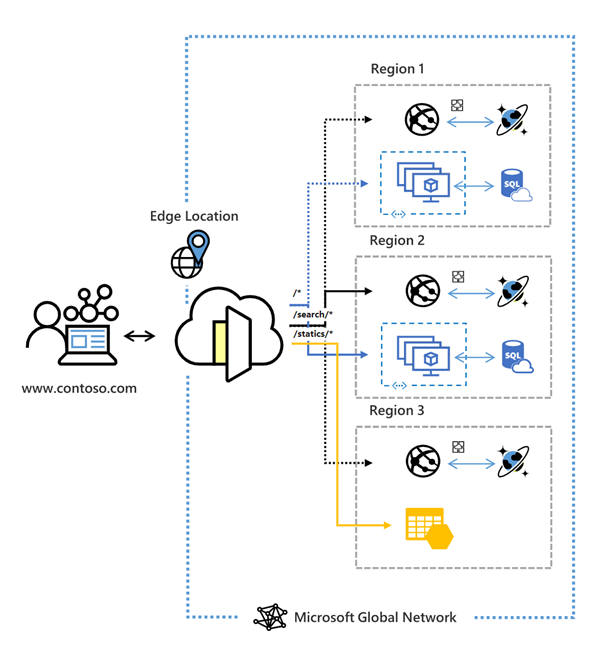
Application delivery services are the features that help you deliver applications in Azure networks, they include Content Delivery Networks (CDN), Azure Front Door Service, Traffic Manager, Application Gateway, Load Balancer, and Internet Analyzer. Azure Front Door service provides the platform to define, manage, and monitor the global routing for your web traffic. It optimizes for best networking performance as well as provides instant global failover to achieve high availability. Implementing Front Door allows you to transform an application to a robust enterprise grade high-performing modern application that can reach a global audience.
What is Azure Network Watcher?
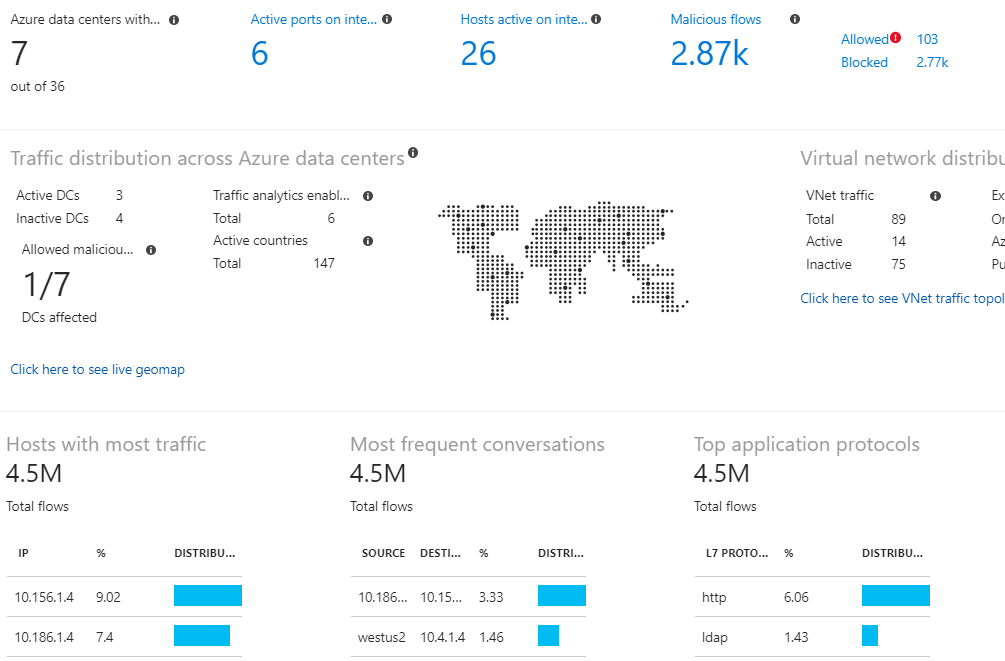
The last group of networking services is Network monitoring. As the name suggests, these features provide the platform to monitor your network resources using any combination of services such as Network Watcher, ExpressRoute Monitor, Azure Monitor, or VNet Terminal Access Point (TAP). Network Watcher is definitely a good tool for Partners that are going to market with Azure. It provides tools to monitor, diagnose, view metrics, and enable or disable logging for resources in an Azure VNet. Network Watcher was designed to monitor and repair the network health of IaaS workloads, but It’s not intended for PaaS monitoring or Web analytics.